NPC probes PhilHealth's possible violations after ransomware attack
MANILA, Philippines — The National Privacy Commission (NPC) said it is investigating the Philippine Health Insurance Corp. (PhilHealth) following a recent ransomware attack that exposed members' personal data.
The NPC is looking into possible violations of data privacy laws and security concerns.
"This decisive action follows the unsettling revelation of a data breach where confidential information was illicitly obtained from PhilHealth's systems," the NPC said in a statement released on Saturday.
The commission expressed their commitment to protecting personal data privacy and launched an immediate investigation into potential breaches by PhilHealth and its officials after a data breach.
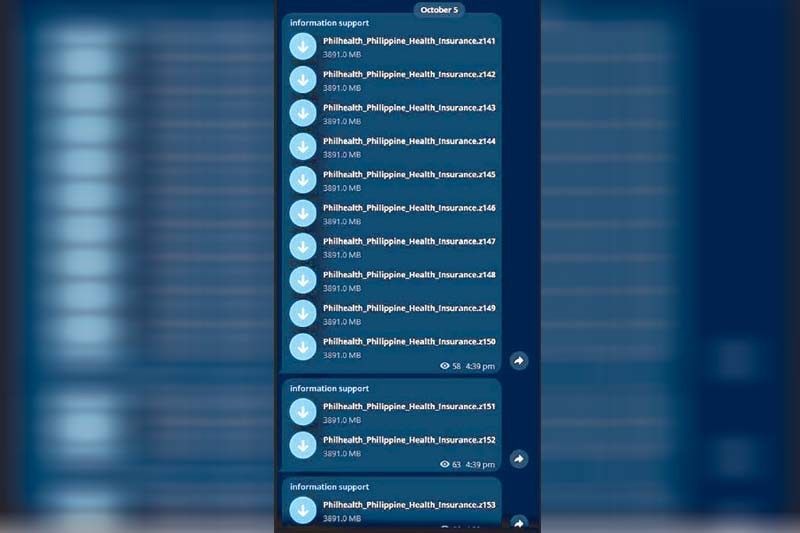
The NPC's Complaints and Investigation Division found a significant amount of personal and sensitive information, totaling 734 GB, in a compressed file claimed by the Medusa group.
The commission has also initiated a “sua sponte” investigation to uncover the full extent of the breach and identify those responsible.
“The NPC will leave no stone unturned in its investigation into the potential negligence of PhilHealth officials and explore whether any efforts have been made to conceal pertinent information,” the privacy body said.
Data stolen from PhilHealth through the Medusa ransomware attack was discovered to have been released online via platforms like Telegram on Thursday.
Previously, PhilHealth acknowledged its inability to determine the exact number of records accessed during the Medusa ransomware attack. However, they expressed the belief that sensitive information was among the data compromised.
The sensitive information includes details such as name, address, date of birth, gender, mobile number and identification number.
PhilHealth has committed to informing affected members whose personal information may have been compromised. It is also urging contributors to take immediate precautions, which include regularly monitoring their credit reports for any unauthorized activities.
The state-managed insurer also advised its members to take the following steps:
- Place a fraud alert on their credit reports to safeguard against potential identity theft.
- Change their passwords across all digital accounts, especially those related to financial platforms.
- Exercise caution and vigilance when handling phishing emails and smishing texts.
Before the data leak occurred, the hackers had demanded a $300,000 ransom in exchange for securing the information.
As a matter of policy, the government maintained its stance of not making any ransom payments to criminal organizations. — with reports by Cecille Suerte Felipe and Elijah Felice Rosales
- Latest
- Trending































